While we have all used digital security certificates like SSL/TLS, code signing certificates, or others, many don’t know the security technology behind them. Stringent security standards ensure that the cyber threats looming around us never get to our digital systems.
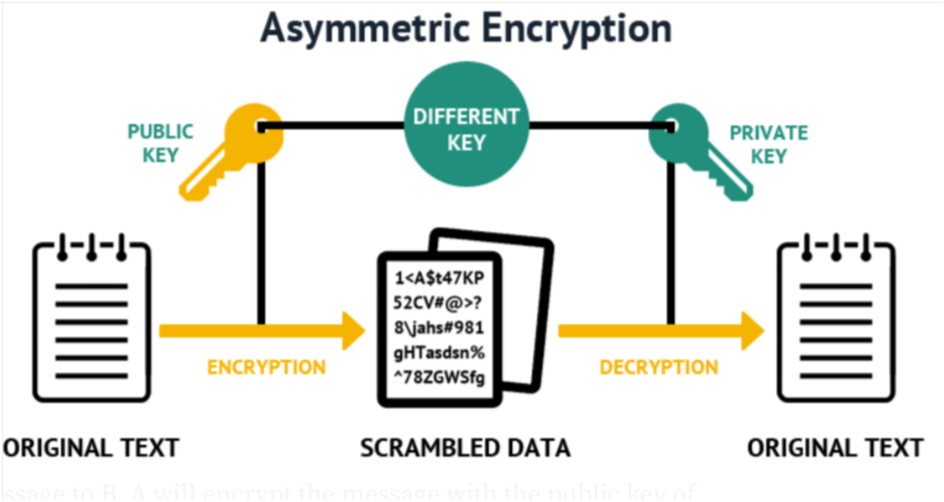
Due to such threats, there’s a constant advancement happening in data security technology to protect sensitive information. Encryption and Signing are two methods used widely for data security. Encryption provides confidentiality where users can encrypt any data with the public key and decrypt it with the private key.
In signing, a digital signature is used for authenticating the data sender. It uses a hashing algorithm along with the public-private key infrastructure for authentication. While both technologies are used for data protection and authentication, there are some differences. Before we get to know what they are, let’s understand encryption and signing in detail:
What Does Encryption Mean & How It Works?
Encryption is a process where data in the form of plaintext is transformed into ciphertext. The ciphertext is created using the encryption algorithm where all the patterns of the plaintext are recreated into a new format of the text that can only be deciphered using a private key.
This key ensures that the data is only decrypted by the authorized recipient. In simple terms, the sender of the data will use the public key to write and send an encrypted message while the recipient uses the private key to read the data.
Encryption comes in two different types: Symmetric and Asymmetric encryption. Asymmetric is the most secure way to protect sensitive information as it involves creating a pair of public and private keys. The private key is kept secret while the public key is available to everyone to decrypt the sent data.
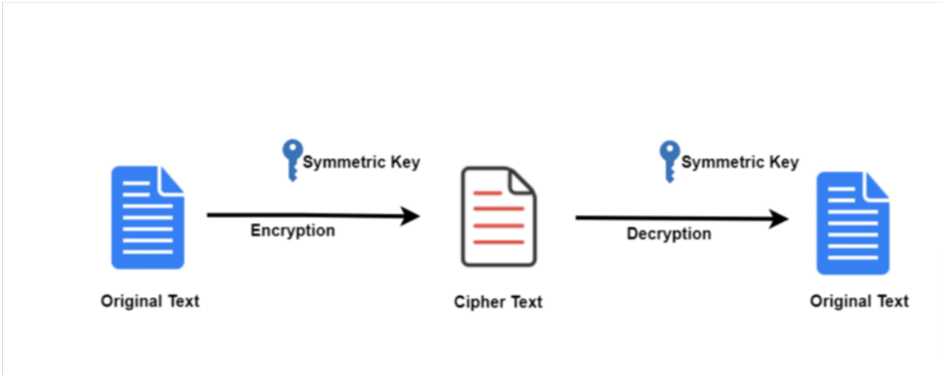
In symmetric encryption, there’s only one key to encrypt and decrypt the sent data, which makes the information vulnerable to attacks. Using encryption technology, businesses can encrypt their emails, documents, user payment information, and other sensitive data.
Be it healthcare, HR, finance, legal, or online shopping, authorities like GDPR, HIPAA, and others make it mandatory for businesses to meet security regulations. And if they fail to do so, they attract big revenue losses and hefty fines from these legal authorities.
What Does Signing Mean & How It Works?
The signing process is where the sender of the data encryption is authenticated to ensure the data is coming from a legitimate source and doesn’t involve malicious code. It also ensures that the data received hasn’t been altered or attacked during the transit.
In simple terms, the signing process involves digital signatures to bind the source with the data while sending it. Here, the sender uses the private key to write and send the data and the receiver uses the public key to check if the data is from the mentioned source or not.
Thus, when a hacker tries to compromise the data with malicious injection, the public key won’t match the private key, letting the recipient know not to trust the source. Such a level of security is only possible with code signing certificates obtained from reputed Certificate Authorities or their trusted code signing distributors.
The digital signing process is somewhat opposite to how encryption works. Here, the hashing algorithm and the sender’s private key are used for digitally signing the data. The process creates the hash digest that can only be recreated using one of the keys from the key pair of the sender.
The sender, then, sends the data, the hash digest, and the public key to the recipient. Now the recipient will use this public key to hash the received information, which should match the hash digest sent along with the data. If it matches successfully, the identity of the sender is then confirmed along with the data which ensures it hasn’t been modified.
Differences Between Encryption and Signing
| Encryption | Signing |
| Encryption technology is used for encoding sensitive information sent in an email or document. | Signing is used for verifying the identity of the source of the information sent over the Internet. |
| There are two encryption methods: asymmetric and symmetric. Asymmetric encryption uses public-private key infrastructure. | Signing uses the hashing algorithm to generate a hash digest that utilizes the public-private keys for sender authentication. |
| Here, the sender uses the public key to encrypt the data while forwarding it to the recipient who uses the private key to decrypt the same. | In digital signing, the sender uses the private key while the public key is used by the receiver to verify the sender’s authenticity. |
| Encryption is enforced by a digital security certificate such as SSL/TLS for sender data verification. | Digital signing is enforced by a digital signature which is stored in a code signing certificate for sender identity verification. |
| Senders need to acquire such certificates from Certificate Authorities (CAs) to successfully encrypt their messages. | Here, the sender also needs to acquire the code signing certificate from CAs like Sectigo or Comodo or their distributors. |
Why Should You Use Digital Signatures?
Digital signatures in the form of code signing certificates are used primarily for identifying and authenticating the individuals or publishers of the message or file. Digital signatures can also help you to safeguard your data from serious threats and vulnerabilities too.
Often encryption and digital signing are used together to protect the data or file from getting compromised while authenticating the sender at the same time. This is because of the need to meet the legal security standards set by GDPR, FIPS, HIPAA, CA/B, and others.
These authorities require companies to secure data with as stringent standards as possible while simultaneously implementing source authentication protocols. Doing so helps give users the peace of mind that the data being sent and received belongs to a legitimate source and isn’t compromised.
Thus, the use of digital code signing certificates and encryption together helps keep the integrity, confidentiality, and authenticity of sensitive data.
Conclusion
Now that you have understood the differences between encryption and the signing process, it’s time for you to get started with securing your data or executable files. Digital signing using a code signing certificate is quite the opposite of how data encryption works as explained above.
Digital signatures have become a necessity today to protect your data from malicious actors while conforming to the standards set by the legal authorities. The publisher of the file or sender of the data can easily obtain the digital signature and certificate from Certificate Authorities or their distributors at affordable rates.
